
|
Chapter 16 |

|
Contents:
Networking
IPv4: The Internet Protocol Version 4
IP Security
Other Network Protocols
Summary
Local and wide area computer networks have changed the landscape of computing forever. Almost gone are the days when each computer was separate and distinct. Today, networks allow people across a room or across the globe to exchange electronic messages, share resources such as printers and disk drives, or even use each other's computers. Networks have become such an indispensable part of so many people's lives that one can hardly imagine using modern computers without them.
But networks have also brought with them their share of security problems, precisely because of their power to let users easily share information and resources. Networks allow people you have never met to reach out and touch you - and erase all of your files in the process. They have enabled individuals to launch sophisticated electronic attacks against major institutions as well as desktop computers in home offices. Indeed, networks have created almost as many risks as they have created opportunities.
The next six chapters of this book discuss UNIX security issues arising from the deployment of computer networks. In this chapter we describe local and wide area networks, and show how they fit into the UNIX security picture.
From a practical viewpoint, computer users today usually divide the world of networking into two halves:
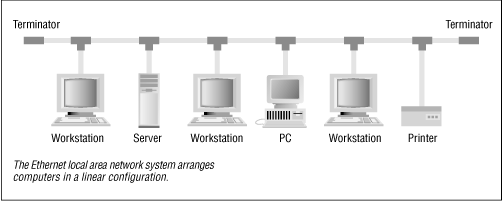
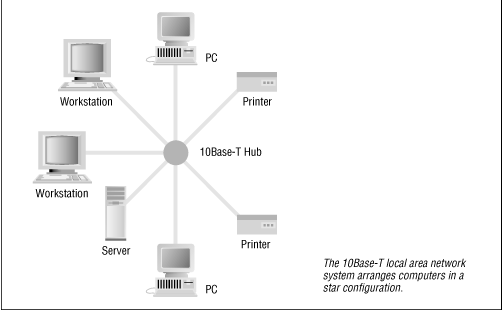
Local Area Networks ( LANS ) are high-speed networks used to connect together computers at a single location. Popular LANS include Ethernet (see Figure 16.1 ), token ring, and 10Base-T (also known as twisted-pair; see Figure 16.2 ). LANS typically run at 10 megabits/sec or faster. LANS capable of 100 megabits/sec are expected to be widely available in the coming years.
Wide Area Networks ( WANS ) are slower-speed networks that organizations typically use to connect their LANS . WANS are often built from leased telephone lines capable of moving data at speeds of 56 kilobits/sec to 1.55 megabits/sec. A WAN might bridge a company's offices on either side of the town or on either side of a continent. Some WANS are shared by several organizations.
Some authors also use the terms Enterprise Networks and Metropolitan Networks ( MANS ). In general, these are simply combinations of LANS and WANS which serve a logically related group of systems.
Many businesses started using LANS in the late 1980s and expanded into the world of WANS in the early 1990s. Nevertheless, the technology to network computers was actually developed in the reverse order: WANS were first developed in the early 1970s to network timesharing computers that were used by many people at the same time. Later, in the early 1980s, LANS were developed, after computers became economical and single-user computers became a financial reality.
[1] We recommend that readers interested in the history of networks read the excellent Casting the Net: From ARPANET to INTERNET and Beyond , by Peter H. Salus (Addison-Wesley, 1995).
One of the first computer networks was the ARPANET , developed in the early 1970s by universities and corporations working under contract to the Department of Defense's Advanced Research Projects Agency ( ARPA , once also known as DARPA ). The ARPANET linked computers around the world, and served as a backbone for many other regional and campus-wide networks that sprang up in the 1980s. In the late 1980s, the ARPANET was superseded by the NSFNET , funded in part by the National Science Foundation. Funding for the NSFNET was cut in the early 1990s as commercial networks grew in number and scope.
Today, the descendent of the ARPANET is known as the Internet. The Internet is an IP-based[2] network that encompasses hundreds of thousands of computers and tens of millions of users throughout the world. Similar to the phone system, the Internet is well connected. Any one of those tens of millions of users can send you electronic mail, exchange files with your FTP file server, or try his hand at breaking into your system - if your system is configured to allow them the access necessary to do so.
[2] IP stands for Internet Protocol, the basic protocol family for packet interchange.
In the early days of the ARPANET , the network was primarily used by a small group of research scientists, students, and administrative personnel. Security problems were rare: if somebody on the network was disruptive, tracking him down and having him disciplined was a simple matter. In extreme cases, people could lose their network privileges, or even their jobs (which produced the same result). In many ways, the Internet was a large, private club.
These days the Internet is not so exclusive. The Internet has grown so large that you can almost never determine the identity of somebody who is breaking into your system: attackers may appear to be coming from a university in upstate New York, but the real story can be quite different. Attackers based in the Netherlands could have broken into a system in Australia, connected through the Australian system to a system in South Africa, and finally connected through the South African system to a New York university. The attackers could then use the New York account as a base of operations to launch attacks against other sites, with little chance of being traced back to their own site. This site hopping is known as network weaving or connection laundering .
Even if you are persistent and discover the true identity of your attacker, you may have no course of action: the attacks may be coming from a country that does not recognize breaking into computers as a crime. Or, the attacks may be coming from an agent of a foreign government, as part of a plan to develop so-called "information warfare" capabilities.[3] There is also a suspected component of activity by organized crime, and by some multinational corporations. In each of these cases, there may be considerable resources arrayed against any attempt to identify and prosecute the perpetrators.
[3] Some authorities speculate (in private) that as many as a third of break-ins to major corporate and government computers in the U.S. may be the result of "probe" attempts by foreign agents, at least indirectly.
UNIX has both benefited from and contributed to the popularity of networking. Berkeley's 4.2 release in 1983 provided a straightforward and reasonably reliable implementation of the Internet Protocol (IP), the data communications standard that the Internet uses. Since then, the Berkeley networking code has been adopted by most UNIX vendors, as well as by vendors of many non -UNIX systems.
After more than a decade of development, the UNIX operating system has evolved to such a point that nearly all of the things that you can do on a single time-shared computer can be done as least as well as on a network of UNIX workstations. Here is a sample list:
Remote virtual terminals ( telnet and rlogin ). Lets you log into another computer on the network.
Remote file service. Lets you access your files on one computer while you are using another.
Electronic mail ( mail and sendmail ). Lets you send a message to a user or users on another computer.
Electronic directory service ( finger , whois , and ph ). Lets you find out the username, telephone number, and other information about somebody on another computer.
Date and time. Lets your computer automatically synchronize its clock with other computers on the network.
Remote Procedure Call ( RPC ). Lets you invoke subroutines and programs on remote systems as if they were on your local machine.